Security Essentials - Managing Today's Risks
Thomas G. Stephens, Jr., CPA, CGMA, CITP
Today’s security issues are more challenging than ever, and tomorrow’s will be even more difficult to manage. But that does not mean that securing sensitive data is a lost cause. Rather, it suggests that we need to take a more focused approach to implementing specific security measures in response to specific security risks. Read on, and in this article, you will learn how you can manage today’s threats by adopting measures designed specifically to mitigate these risks.
Controlling Access Risk
Though it is stating the obvious, if we can keep the cybercriminals out of our computers, networks, and databases, then we can protect the data contained on each of these devices. This type of risk is known as access risk and it involves ensuring that the cybercriminals do not have physical or logical access to our systems and the data contained therein. Regarding physical access risk, the solution is simple – do not allow unauthorized parties to come into contact with your devices. This means deploying “common sense” physical controls such as keeping your servers and other sensitive equipment in restricted-access and locked facilities such that only authorized persons have direct physical contact with these assets.
Implementing effective logical access controls is a bit more challenging than implementing effective physical access controls. Regarding logical access controls, it would be nice to think that usernames and passwords would be sufficient, but these rely on humans and we must assume that humans are going to make mistakes – mistakes that could cause their login credentials to become compromised. Therefore, to adequately address logical access risk, you should take steps such as implementing multi-factor authentication (MFA) whenever you can do so. MFA involves logging-in to a device or system by using at least two of the three items listed below.
- Something you know, such as a username and/or a password.
- Something you have in your possession, such as a smartphone or a key fob to which an additional log-in code could be sent upon successfully entering a username and password.
- Something you “are,” such as a fingerprint, facial recognition, or retina scan.
By implementing MFA through requiring a username and password in addition to an additional log-in code sent to your smartphone, a cybercriminal would not only have to compromise your username and password, but the bad actor would also have to have possession of your smartphone to receive the additional log-in code sent to the device. While it is not impossible that all these conditions could materialize, it is highly unlikely and because of this, the risks associated with logical access are significantly reduced.
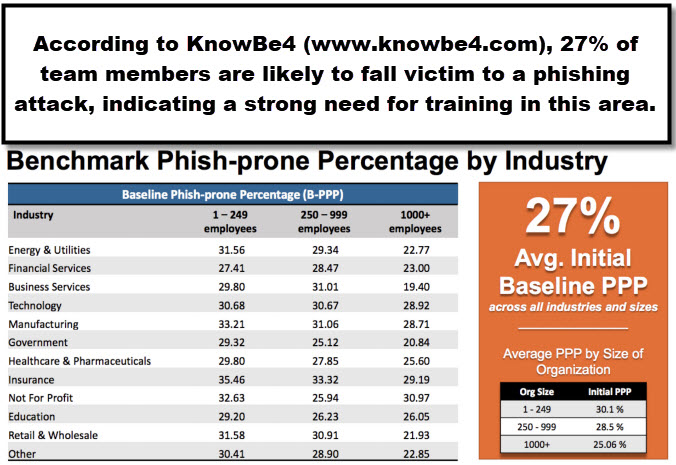
Thwarting social engineering attacks
Social engineering involves cybercriminals attempting to trick your team members into surrendering sensitive information – oftentimes usernames and passwords – so that they can use that information either to further an attack or to profit directly from the information. A common scheme is for the cybercriminal to call an individual and pose as a member of the company’s information technology team, indicating to the team member that there is a “problem” with the team member’s email account. The cybercriminal would go on to explain to the team member that she needs his username and password to log-in to the team member’s email account so that she can fix the problem. Of course, once she receives the username and password from the team member, she uses it to further some other nefarious activity. Other examples of social engineering attacks involve sending emails with malicious links or attachments in the hopes that the recipient will click on these links or attachments to install malware.
To reduce the risk of social engineering attacks such as these, team members should be thoroughly trained to recognize the types of situations described above and to “just say no!” Under no circumstances should a team member ever share usernames and passwords with others, including their managers or members of the information technology team. Likewise, under no circumstances should any individual ever ask for another team member’s credentials. We must create a more security-aware culture so that the specific risk of social engineering attacks is diminished and that in general, all team members have a heightened awareness regarding their role in the security regime of the organization.
Stopping violations of company security policies
Many companies have adopted various forms of security policies, including policies indicating that items such as Social Security numbers, bank account numbers, and other sensitive data should never be transmitted through unencrypted email messages or stored in shared folders on the company’s servers. Yet countless studies indicate that team members ignore policies such as these at alarmingly high rates. To prevent violations of company policies surrounding sensitive information, consider implementing Data Loss Prevention (DLP) tools.
DLP tools allow an organization to specify what type of data can be stored or transmitted through its resources. Included in virtually every DLP tool available today is the ability to block – among other things – outbound email messages that contain sensitive information such as Social Security numbers, credit card account numbers, and other types of information that should remain private. Many business-oriented email servers and services such as Exchange Server, Exchange Online, and G Mail provide built-in access to DLP tools that focus on blocking email traffic containing sensitive information. You can deploy other commercially-available DLP solutions to analyze traffic across your network or data that is stored on your servers for violations of company policies. All told, DLP is one of the best – and least expensive – means of ensuring that team members comply with your company’s security policies and standards.
Reducing the risk of ransomware
Ransomware is a particularly insidious form of an attack on your data. If you become a ransomware victim, your data will be taken hostage until you pay a ransom, and even then, you are not likely to be provided with access to your data. To reduce the risk of ransomware, consider activating Controlled Folder Access (CFA), a feature that was added to Windows 10 in September of 2017. With CFA enabled, Windows protects documents in folders that you specify so that unauthorized applications cannot alter these documents. By applying this “whitelisting” approach to preventing a ransomware attack, even if the ransomware gets installed onto your computer, the risk to your data remains relatively small. Controlled Folder Access is one of the easiest – and best! – ways of mitigating ransomware risk.
SUMMARY
Yesterday’s security techniques are no match for today’s risks, but that does not mean that we must be resigned to accepting unnecessarily high risks either. By identifying where your biggest risks are and taking a targeted approach to addressing these risks, we can mitigate them to a prudently-acceptable level. Pay particular attention to the four risks and – more importantly – the four solutions outline above and both you and your team will be in a better position to protect the sensitive information to which you have been entrusted. Good Luck!
In addition to being a CPA, Mr. Stephens is a shareholder in K2 Enterprises, LLC , where he develops and presents continuing professional education programs on a variety of subjects, including information security. You may contact him at tommy@k2e.com.